Role: Senior UX / Product Designer
Domain: Identity & Access Management (IAM), SaaS
Focus: UX × AI × Security
Outcome: Reduced friction, improved trust, scalable access experience
In many SaaS products, Identity & Access Management (IAM) is designed as a security layer not as a user experience.
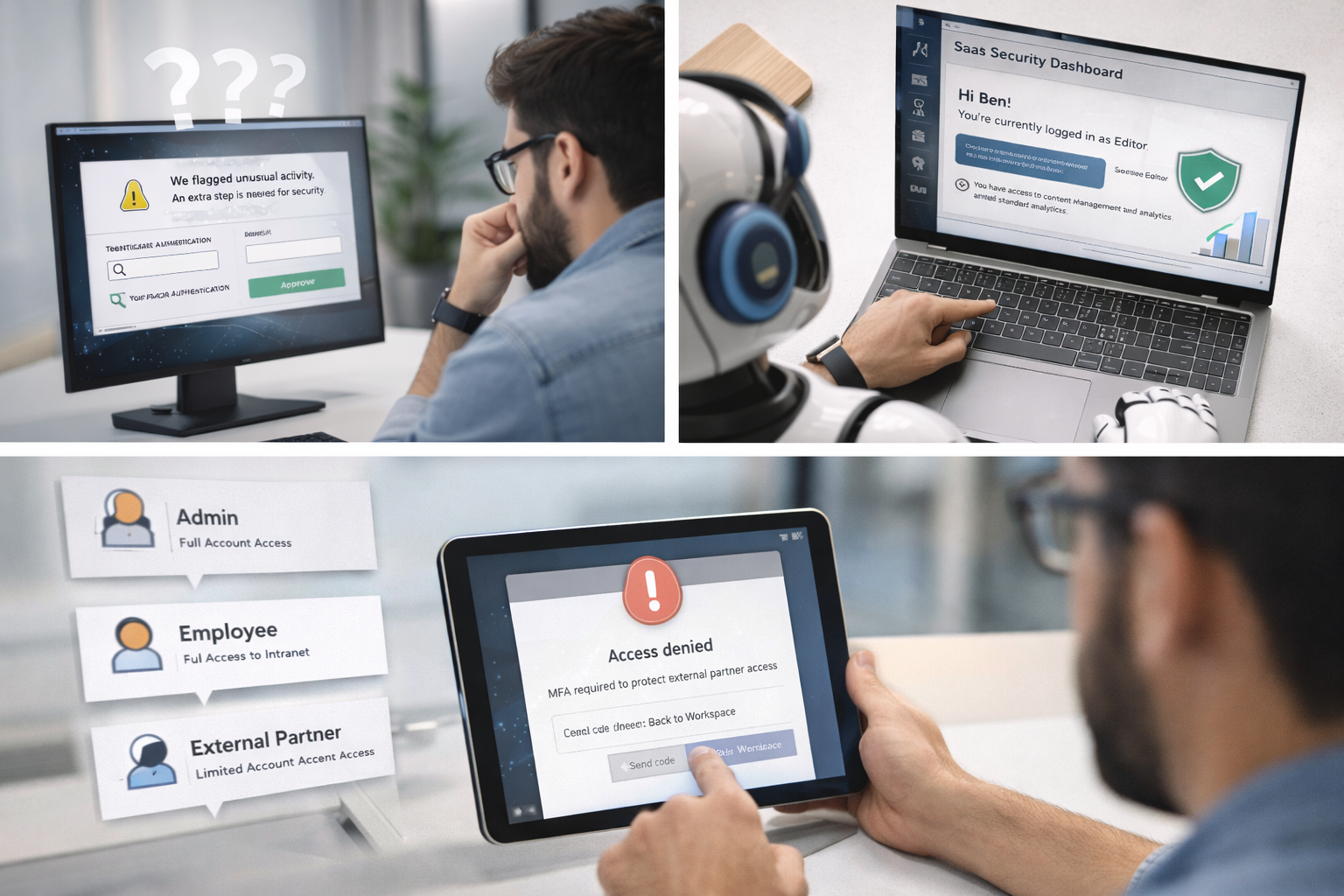
Users commonly face:
While systems remain secure, the experience creates:
How might we design IAM experiences that remain highly secure without feeling hostile or disruptive to users?
IAM operates at the intersection of:
Key constraints:
This required a systems-thinking approach, not surface-level UI fixes.
Security doesn’t need to be louder, it needs to be smarter and clearer.
If AI can make risk-aware decisions in real time,
UX can translate those decisions into predictable, trustworthy experiences.
Hypothesis:
Combining AI-driven context with human-centered UX can reduce friction without reducing security.
Users don’t experience AI models.
They experience moments of interruption.
Those moments define trust.
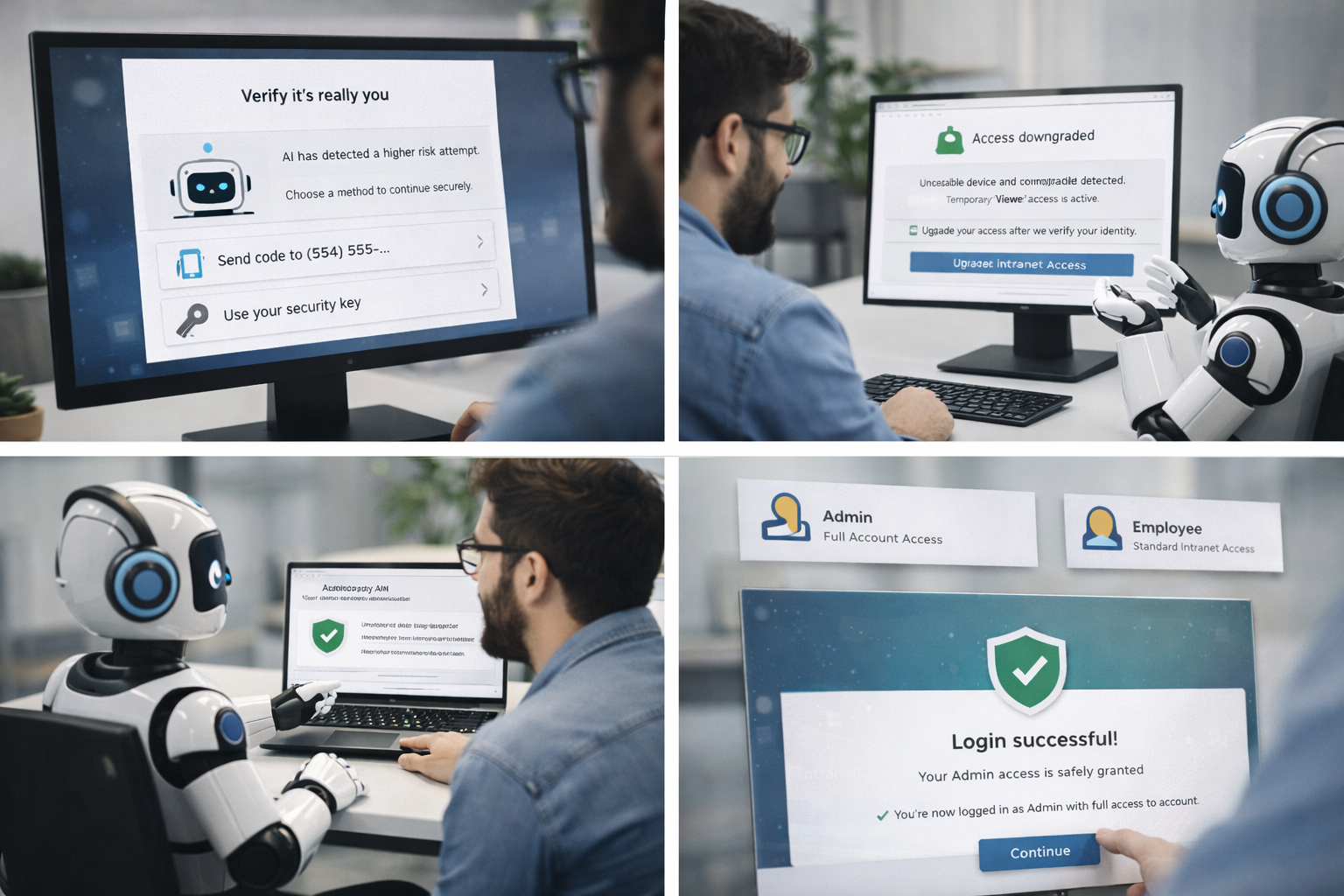
Instead of treating AI and UX separately, the system was designed as a collaborative loop:
Security decisions stayed strong the experience changed.
1. Adaptive, Not Static
Authentication adjusts based on real-time risk instead of fixed rules.
2. Predictability Over Surprise
Users are guided with expectations rather than interrupted randomly.
3. Explain Without Overloading
Clear, human explanations without exposing sensitive logic.
4. Respect the User’s Flow
Security adapts to users, users don’t fight the system.
While exact metrics vary by implementation, the design intent focused on:
Security felt supportive, not punitive.
This project highlights my approach to:
Designing complex, high-risk systems
Working at the intersection of UX, AI, and security
Thinking beyond screens into behavior and trust
Balancing business risk with human experience